Sextortion is a new age cyber abuse that threatens reputational loss of the victim. The entire cybercrime is rooted in manipulation and blackmailing for extorting personal favours and money. The issue is more concerning as often victims are too afraid or ashamed of reporting sextortion cases.
With access to high-speed data at cheaper rates and heavy usage of social media platforms, sextortion cases are reporting a steep surge. Organizations may get affected too in case the offenders ask for business information as ransom or try maligning the brand’s name by releasing inappropriate pictures/ videos of an employee. Therefore, it is necessary that both organisations and
employees undertake appropriate precautions and practice due diligence while engaging in online activities.
Modus Operandi-
Four Phases of Victimisation
- Target Victims – Often those using dating or social media apps without much cybersecurity checks in place.
- Gather Information – Either by befriending the target or using malpractices like hacking.
- Convincing Phase – By manipulating and winning the trust of the targets on pretext of being a friend or a well-wisher.
- Harassment – Blackmailing the victims using sensitive/personal information against them to further draw compromised contents, personal favours or even ransom.
Modes of Victimisation
- Dating Apps
- Social Media Platforms (Facebook, Instagram,etc)
- Instant messaging apps and Emails (WhatsApp, Snapchat,etc)
- Phishing and Hacking
- Direct SMS using fraudulent links
- Gaming Platforms
- Acquaintance or known contacts
Target Victims

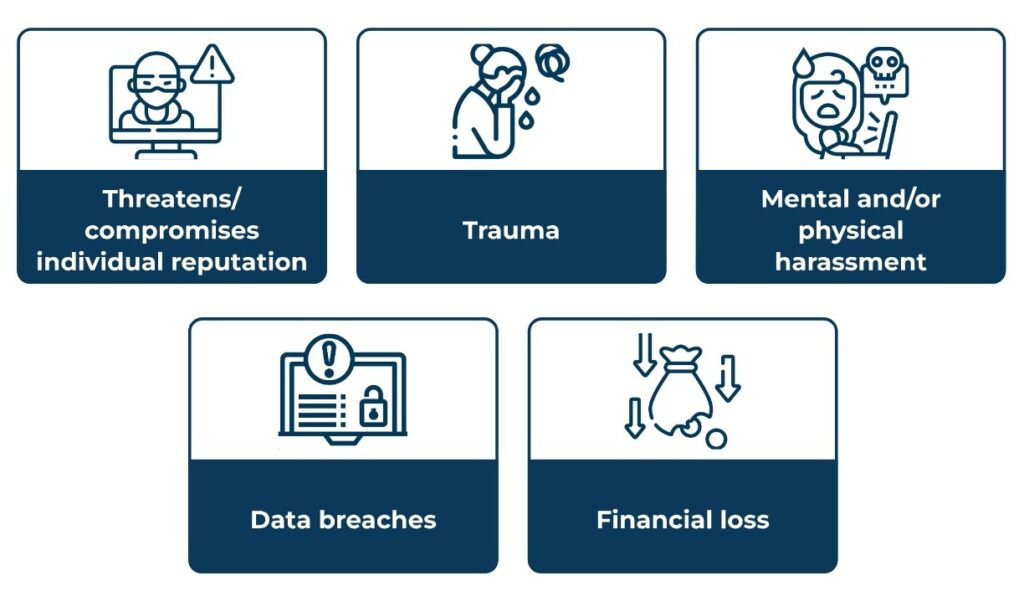
Impacts

Safety Tools on Social Media Platforms
- Run a Privacy Checkup on Facebook to control what is being shared with whom. For more details on safe Facebook practices, refer to Avoid Spams and Scams.
- Privacy, Intellectual Property violation or any form of abuse on Facebook can be reported using Reporting Abuse feature.
- Problematic content or spam can be reported at Block and Report Contacts.
- For further details on safe WhatsApp practices, refer to MitKat’s Special Advisory on WhatsApp Scams and Safety Measures.
- Similarly, abuse or breaches on Snapchat and Instagram can be reported at Report Abuse on Snapchat and Abuse and Spam sections.
Recommendations
For Organizations
- Advised to regularly update internal cybersecurity mechanism, invest in good antivirus software on office appliances.
- Ensure strict hygiene checks of online activities of employees using office devices or official email/social media accounts.
- Host knowledge sessions to generate awareness on cybersecurity and safe social media practices.

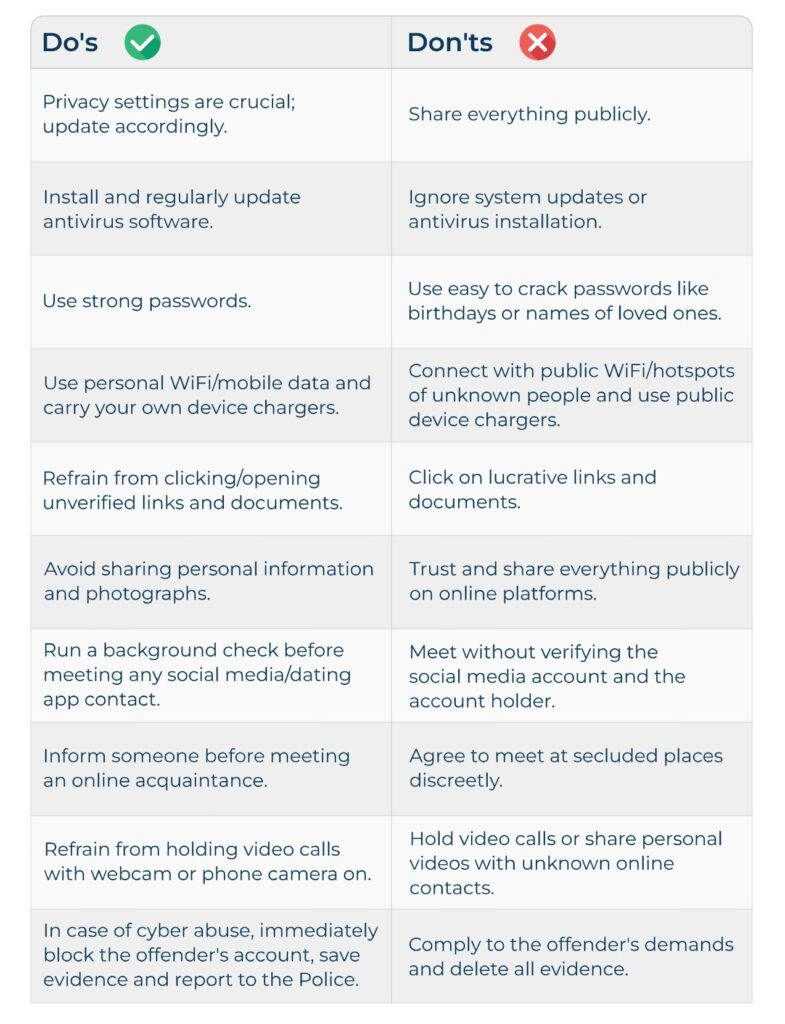
For Individuals

Important Contacts and Links in India-
- National Cyber Crime Reporting Portal – https://cybercrime.gov.in/
- Cyber Crime Helpline – 1930
- National women helpline number – 181
- National police helpline number – 112
- Report and remove compromised contents on minors – Take It Down
- Report Cybercrimes against women – Complaints Registration and Monitoring System or call +91-11-26944880/ +91-11-26944883.
- For updates on cyber safety and cyber security awareness – Cyber Dost




